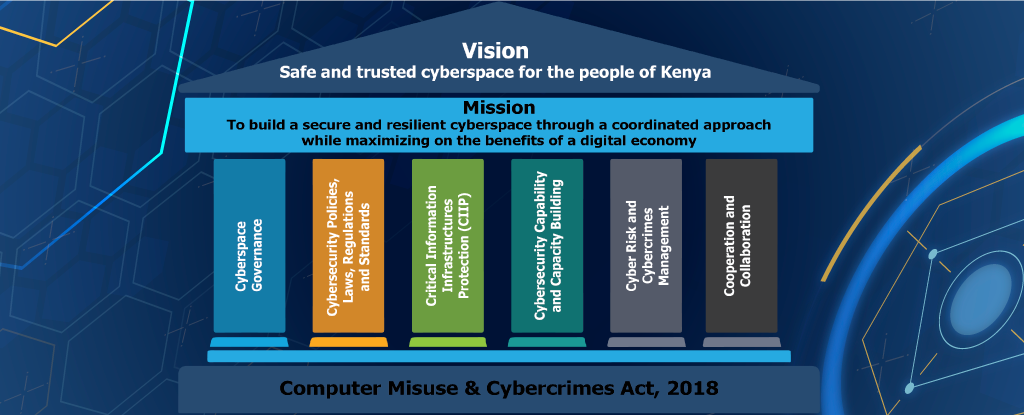
The wide adoption and increased reliance on digital technologies in Kenya have created new risks that expose individuals, businesses, national infrastructure, and government to cyber threats emanating from malicious state and non-state actors.
The most prevalent threats include cyber espionage, subversion through propaganda and misinformation, cyberterrorism activities, and cyber fraud cases. Through this Strategy, the Republic of Kenya affirms its commitment to addressing cybersecurity challenges and threats. This will be achieved by establishing governance structures, strengthening policy, legal and regulatory frameworks, enhancing the protection of Critical Information Infrastructure (CII), capability and capacity building, minimizing cybersecurity risks and crimes, and fostering collaboration.
Since Cybersecurity is a shared responsibility, both public and private stakeholders will synergize their efforts toward achieving a safe and trusted cyberspace for the people of Kenya.
Strategy Goals
The following are the goals of the Strategy:
- Enhance Kenya’s institutional framework for cybersecurity
governance and coordination. - Strengthen cybersecurity policy, legal, and regulatory frameworks.
- Enhance the protection and resilience of CIIs.
- Strengthen cybersecurity capability and capacity.
- Minimize cybersecurity risks and crimes.
- Foster national and international cooperation and collaboration.
Guiding Principles
The guiding Principles of the Kenya Cybersecurity Strategy 2022 are based on the following objectives of the Computer Misuse and Cybercrimes Act, 2018:
- Protect the confidentiality, integrity, and availability of computer systems, programmes, and data;
- Prevent the unlawful use of computer systems;
- Facilitate the prevention, detection, investigation, prosecution, and punishment of cybercrimes;
- Protect the rights to privacy, freedom of expression, and access to information as guaranteed under the constitution of Kenya 2010; and
- Facilitate international cooperation on cybersecurity matters.