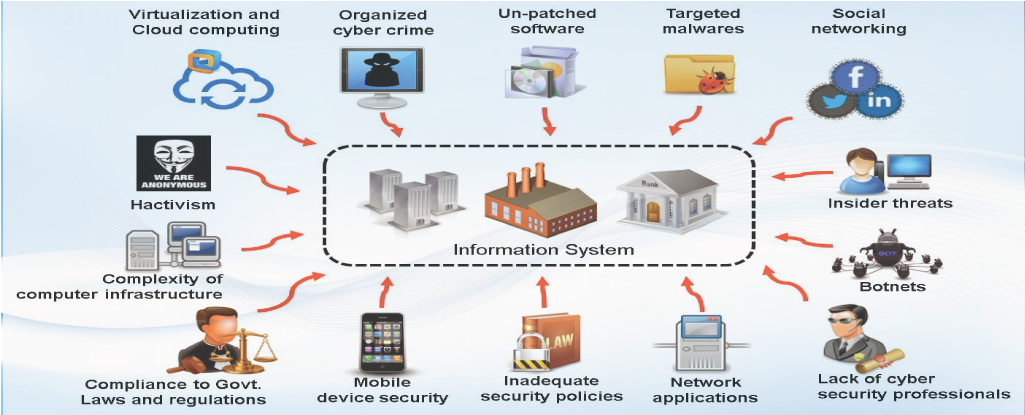
Attack vectors help unauthorized elements to exploit the vulnerabilities in the system or network, including the human element. Examples of attack vectors are email attachments, pop-up windows, deception, chat rooms, viruses, and instant messages.
Attack surface
The sum-total of points on a network where attacks can occur where an unauthorized user (the “attacker”) can try to manipulate or extract data using a myriad of breach methods (the “cyber-attack vectors”). If you consider a graph, where the x-axis lists all of the devices and apps on your network (infrastructure, apps, endpoints, IoT, etc.) and the y-axis are the different breach methods such as weak and default passwords, reused passwords, phishing, social engineering, unpatched software, misconfigurations, etc. the plot is your attack surface.

Cyber Attack vector
The method or ways by which an adversary can breach or infiltrate an entire network/system. Attack vectors enable hackers to exploit system vulnerabilities, including the human element of which is the weakest element.